With the release of macOS 26 Tahoe, Apple has introduced one of the most impactful features for IT admins and power users: the ability to unlock a FileVault-encrypted Mac remotely over SSH after a reboot.
***Until now, FileVault presented a practical challenge. A rebooted Mac with FileVault enabled remained inaccessible until someone physically entered credentials at the login screen. For administrators managing headless Macs, CI/CD build servers, remote workstations, or enterprise fleets, this limitation often meant downtime, delays, or even costly workarounds like hardware KVMs.***
How It Works
When FileVault is enabled, the system volume stays encrypted until a local account password is entered. Normally, SSH and configuration files aren’t available until after login.
In macOS Tahoe, however, Apple has built a minimal SSH environment that runs even before FileVault is unlocked:
- From another machine, you connect via SSH:

- Instead of a normal login, you’ll see: “This system is locked. To unlock it, use a local account name and password.”
- Enter the correct credentials.
- The system responds: “System successfully unlocked. You may now use SSH to authenticate normally.
At this point, the Mac:
- Mounts the encrypted data volume.
- Restarts dependent services.
- Returns to standard SSH accessibility.
- Moves the local display to the login window.
Important Limitations
This feature comes with some boundaries admins need to know:
- IP Address Required – You must know the Mac’s IP before attempting SSH.
- 802.1X Wi-Fi Not Supported – Certificates stored in the system keychain aren’t accessible until FileVault is unlocked, limiting use in enterprise Wi-Fi setups.
- Temporary Disconnect – SSH will briefly drop after unlocking while the system reinitializes services.
Security: Lockout Protection
Apple has layered in protections against brute-force attempts.
- If you repeatedly enter the wrong password, the system responds with:
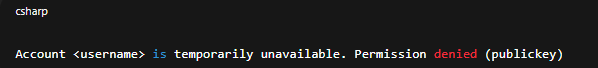
- This lockout temporarily disables further attempts, forcing you to wait before retrying.
- Once the lockout expires, correct credentials can be used again.
Why This Matters
The significance of this feature varies across different use cases:
- IT Admins & Enterprises – Enables remote remediation without physical access, especially for headless Macs or systems hosted in data centers.
- Remote Workers – Provides flexibility to recover from reboots without being on-site.
- Secure Environments – Strengthens device management while keeping FileVault’s encryption intact.
- For teams running Mac minis as CI/CD servers, render farms, or media centers, this unlocks (literally) a new era of hands-off, fully remote management.
As one developer put it:
“I can now have a fully remote Mac mini server with auto-reboot on power outage without needing to physically log in.”
The Road Ahead
This feature is more than a convenience—it’s a signal. Apple is acknowledging the needs of enterprise admins, DevOps Engineers, and remote professionals who rely on Macs in always-on environments.
Next steps to watch:
- Integration with MDM platforms like Jamf for automated workflows
- Support for key-based authentication in future versions
- Refined enterprise tooling around lockout policies and audit logging
Takeaways:
Unlocking FileVault over SSH in macOS Tahoe removes a major roadblock in remote Mac management. It’s a small addition with massive implications, turning previously complex workarounds into a single command.
For IT admins, DevOps engineers, and organizations relying on Macs in critical workflows, this is more than a quality-of-life upgrade—it’s a strategic shift in how macOS can be deployed and maintained at scale.
Remote Mac administration just entered a new era. TexArxs helps businesses harness features like FileVault over SSH to scale, secure, and streamline IT operations like never before.


